Data Foresight Remediation
Data remediation is the process of identifying, correcting, and eliminating inaccurate, outdated, or non-compliant data from an organization’s repositories. This practice ensures data accuracy, integrity, and security while maintaining compliance with regulatory standards such as DPDP, GDPR, CCPA, and HIPAA.
The Importance of Data Remediation

Compliance with Regulations
With the increasing stringency of data protection regulations, maintaining compliance is essential to avoid substantial fines and penalties. Data remediation plays a critical role in ensuring that sensitive information is properly stored, accessed, and utilized in accordance with legal and regulatory requirements.

Enhanced Data Quality
Low-quality data can result in flawed decision-making and reduced operational effectiveness. Data remediation addresses these issues by eliminating duplicates, correcting inaccuracies, and updating outdated information, thereby enhancing data quality and enabling more accurate, reliable insights.

Risk Mitigation
Eliminating unnecessary or improperly stored data enables organizations to minimize the risk of data breaches, unauthorized access, and other security vulnerabilities, thereby strengthening overall data security and compliance posture.

Operational Efficiency
Cleaning and organizing data minimizes system clutter, enhances storage efficiency, and boosts overall performance—resulting in faster response times and more seamless data access.
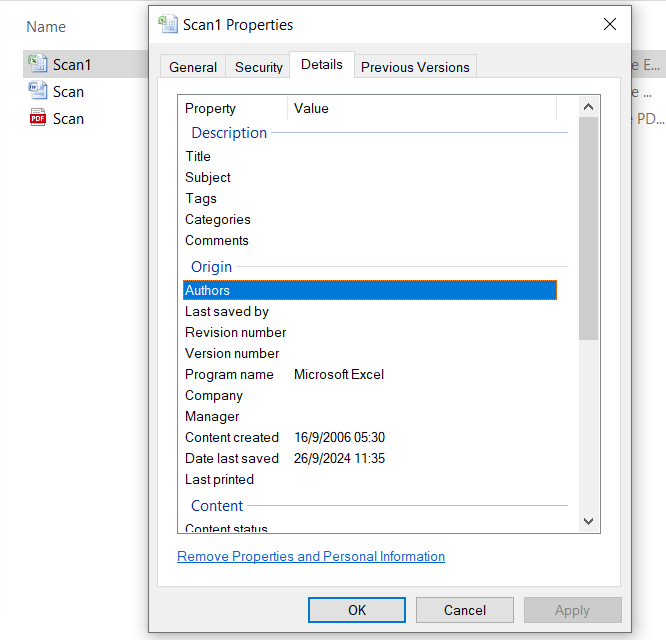
Unclassified File
An unclassified data file is one that does not contain sensitive, confidential, or classified information, and as such, is not subject to security restrictions or special handling protocols. Examples of unclassified files may include publicly available reports, marketing collateral, non-sensitive company policies, or general internal communications.
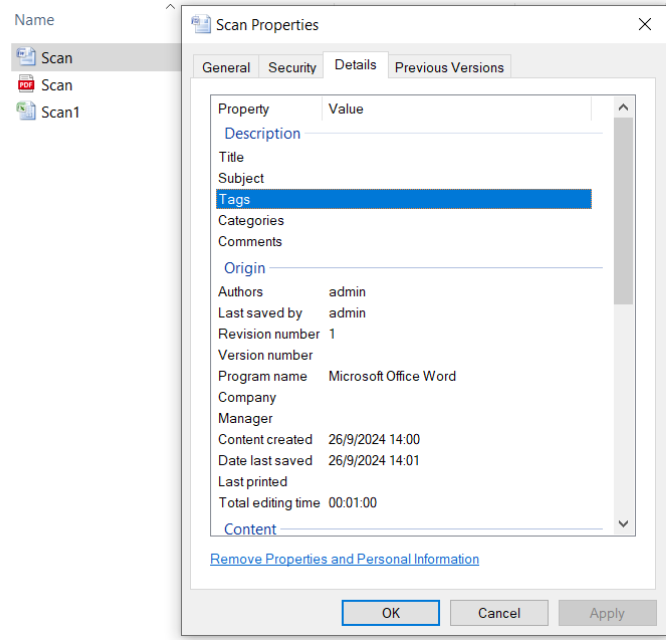
Classified Files
Classified files refer to data considered sensitive and restricted due to the potential risks they pose to national security, corporate operations, or individual privacy if accessed by unauthorized parties. Commonly used in government, military, and large enterprises, this designation indicates that the information requires elevated protection and controlled access based on security clearances or designated permissions.

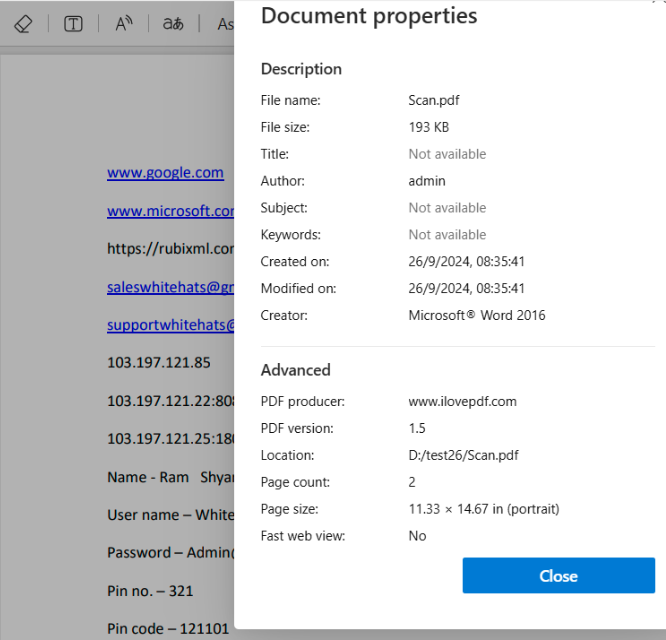
Unencrypted Data
Unencrypted data, often referred to as plain text or clear text, is information that is stored or transmitted without any encryption or protective measures. As a result, it remains in a readable and accessible format, making it easily viewable and interpretable by anyone who gains access, without the need for a decryption key.


Encrypted Data
Unmasked Data
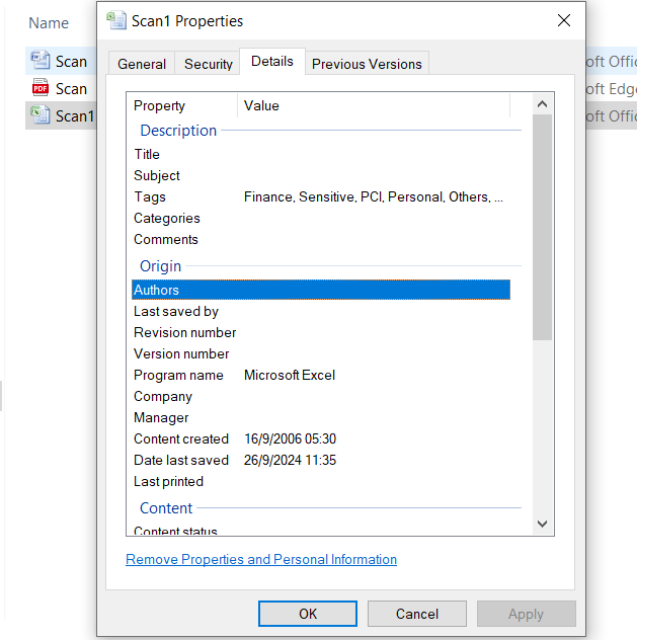
Unmasked data is sensitive or personally identifiable information (PII) that remains in its original, unprotected form, without masking or encryption. This makes it vulnerable to unauthorized access, increasing the risk of data breaches and identity theft. Protecting unmasked data is critical for privacy and compliance with regulations like DPDP, GDPR, HIPAA, and CCPA.


Masked Data
Data Deletion
Data deletion is the process of permanently eliminating information from organizational systems, ensuring it is no longer accessible or recoverable. Unlike data archiving, which preserves data for future retrieval, data deletion is intended to fully erase information to meet regulatory obligations, safeguard sensitive data, and optimize storage utilization.


Deletion Action

Delete file
The Delete File function ensures the secure and permanent elimination of sensitive data from systems, effectively preventing unauthorized access or recovery. This capability is critical for safeguarding data privacy, meeting compliance requirements, and minimizing the risk of data breaches.
Transfer to Vault
The Transfer to Vault function securely relocates sensitive data to a highly protected, encrypted storage environment, restricting access exclusively to authorized users. This approach enhances data security by isolating critical information, supporting regulatory compliance, and reducing the risk of data breaches.